For a system administrator keeping the SSH access to secure the server is always challenging. In this article, I will show you how to tighten your SSH server with a simple two factor authentication by using Google Authenticator. Google Authenticator helps you to secure the SSH access to the server by a two-factor authentication. Initially you need to integrate the SSH daemon on the server using Google Authenticator’s one time password Algorithm (TOTP). Time-based One-time Password Algorithm (TOTP) is an algorithm that computes a one-time password from a shared secret key and the current time. To receive the verification code you have to begin with installing the Google authenticator app into your Smartphone (Android, Iphone, Windows, Blackberry). If you want to access the server, you should carry the mobile with you in order to receive the Authentication code in the mobile.
Table of Contents
Step 1:
First, I would recommend checking whether the NTP (Network Time Protocol) is running to ensure the server’s time is synchronized as Google Authenticator uses time-based codes/tokens that will fail if server time is not correct. So, check the NTP status.If NTP service is already running in the server, go to google-authenticator installation in step 2. If not, follow the instruction in the step given below.Check whether the NTPD service is running: # pgrep ntpd 3102If nothing shows up, NTP is not running. So, install it: #yum install ntpEnsure that the NTP is configured to start automatically during the system startup. #chkconfig ntpd onSync the time: # ntpdate pool.ntp.orgStart the NTP service # service ntpd start
# pgrep ntpd 3102If nothing shows up, NTP is not running. So, install it: #yum install ntpEnsure that the NTP is configured to start automatically during the system startup. #chkconfig ntpd onSync the time: # ntpdate pool.ntp.orgStart the NTP service # service ntpd start
Step 2:
Install open source Google Authenticator PAM module.If ‘yum install google-authenticator’ says there is no package available try to install the EPEL repo for Centos. # Cd /root/ # wget http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm # wget http://rpms.famillecollet.com/enterprise/remi-release-6.rpm # rpm -Uvh remi-release-6*.rpm epel-release-6*.rpmNow you can install Google Authenticator via yum. # yum install google-authenticator
# Cd /root/ # wget http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm # wget http://rpms.famillecollet.com/enterprise/remi-release-6.rpm # rpm -Uvh remi-release-6*.rpm epel-release-6*.rpmNow you can install Google Authenticator via yum. # yum install google-authenticator
Step 3:
Next you need to enable the Google authenticator PAM module, edit your /etc/pam.d/sshd file and add auth required pam_google_authenticator.so and disable auth substack password-auth. Now the file looks like this: # nano /etc/pam.d/sshd#%PAM-1.0 auth required pam_sepermit.so auth required pam_google_authenticator.so # auth substack password-auth account required pam_nologin.soThe Password-auth rule is disabled because you require a key plus a Google Authenticator code, not a password.
# nano /etc/pam.d/sshd#%PAM-1.0 auth required pam_sepermit.so auth required pam_google_authenticator.so # auth substack password-auth account required pam_nologin.soThe Password-auth rule is disabled because you require a key plus a Google Authenticator code, not a password.
Step 4:
The next step is to update the sshd configuration file in /etc/ssh/sshd_config. Change the ChallengeResponseAuthentication line to enable.# nano /etc/ssh/sshd_config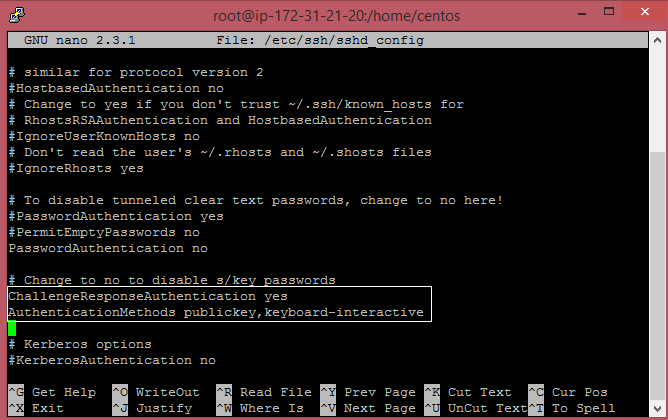 ChallengeResponseAuthentication yesThen you have to add the following line to use your public key and two-factor authentication. AuthenticationMethods publickey,keyboard-interactive
ChallengeResponseAuthentication yesThen you have to add the following line to use your public key and two-factor authentication. AuthenticationMethods publickey,keyboard-interactive
Step 5:
Next, you should configure the users who should be demanded a two-factor authentication.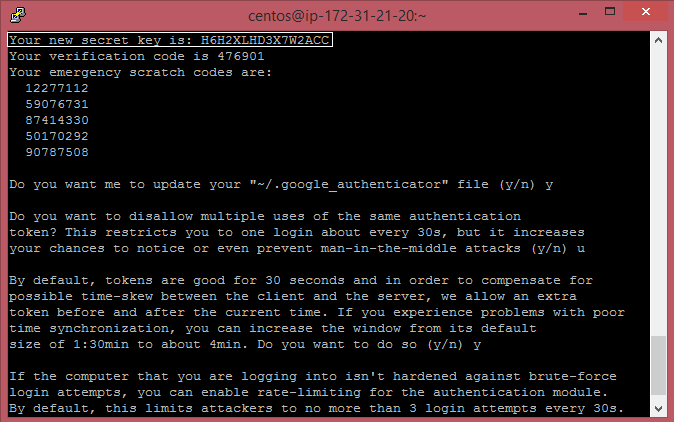 # google-authenticatorYour new secret key is: H6H2XLHD3X7W2ACC Your verification code is 476901 Your emergency scratch codes are: 12277112 59076731 87414330 50170292 90787508
# google-authenticatorYour new secret key is: H6H2XLHD3X7W2ACC Your verification code is 476901 Your emergency scratch codes are: 12277112 59076731 87414330 50170292 90787508
Step 6:
Once you have created a Secret key, restart sshd service to apply your changes. #service sshd restart
Step 7:
Smartphone App Installation. Then you have to install Google authenticator app in your mobile (Android, Iphone, Windows, Blackberry). You can enter the provided key and then add any account name, enter the verification code and then click add.
Step 8:
Finally test the service by connecting with SSH to the server to see if it will require verification code. Of course it works.


hi, is the pub key on .ssh/authorized_keys still on there or is it ok to remove pub key on .ssh/authorized_keys? Thanks